Application Security Posture Management is a set of practices complemented by tools and strategies around security testing and code scanning to create and manage a robust defence against security threats.
ASPM tools provide insights into the current security posture of applications besides providing risk assessment and threat remediation capabilities.
Enterprises can set up ASPM practices by following 10 simple steps to overcome Application Security (AppSec) challenges.
Create Inventory of Applications and Their Components with SBOM
A software supply chain is composed of the components, libraries, tools, and processes used to develop, build, and publish an artifact. Developers often create products / services by assembling open-source and commercial software components.
ASPM tools bring these capabilities to generate the inventory of all the building blocks that make up a software product
You can leverage the Software Bill of Materials (SBOM) to get insights into the structure and specific components of your application. And, if you are able to get these insights the way forward is going to be very easy in lots of aspects.
Similarly, a Delivery Bill of Material (DBOM) can help you get insights into the components that actually got deployed.
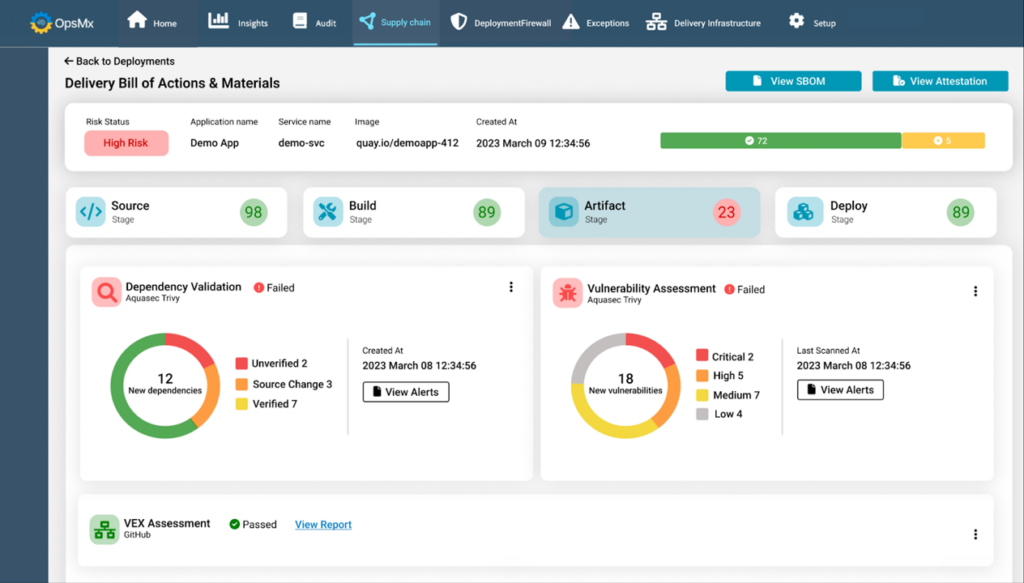
This brings you the capability to run a smart diff to do a provenance check on artifacts / components or specific configurations.
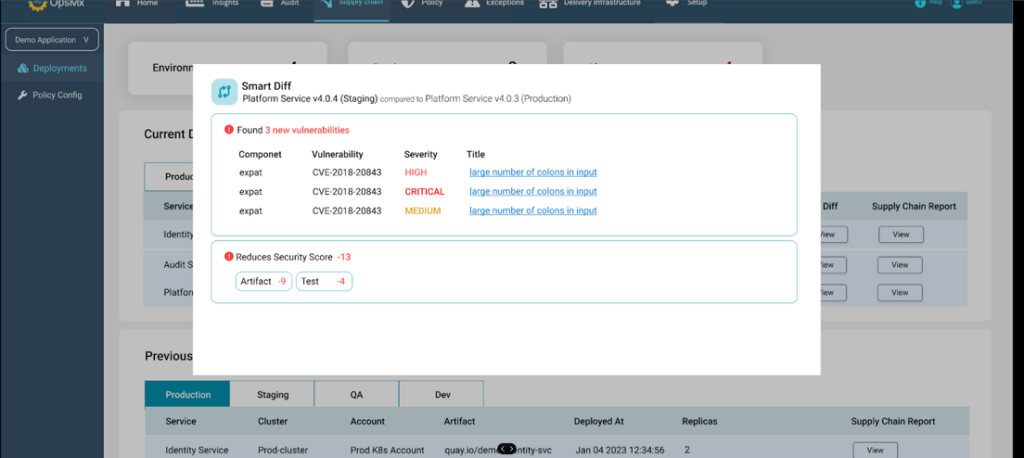
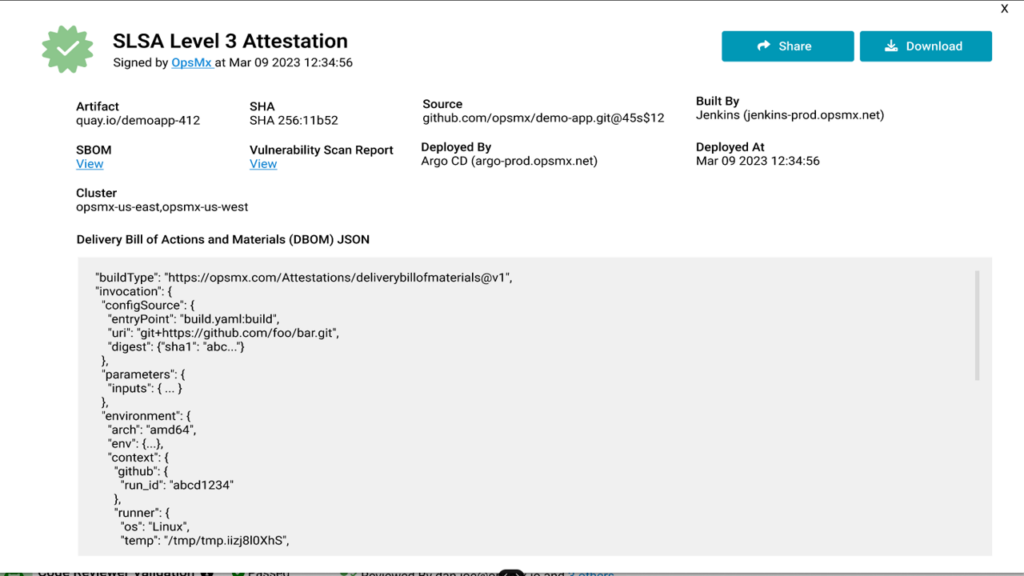
Importantly, if you have the capability to attest an artifact, you can ensure that you deployed the right component – that was meant to be deployed.
Integrate ASPM into SDLC
To build a robust ASPM mechanism integrate testing and scanning into your pipelines, especially build, deploy, and create a framework for automated approvals and compliance automation.
This would help you in creating a repeatable and a scalable model to enable early detection and remediation of vulnerabilities. This will help you to bring down the cost of remediation.
To operationalize the analysis and enforcing compliance, you need 3 important components – set of rules, data and the enforcement layer to automate security compliance.
Vulnerability Scanning for Application Level Security View
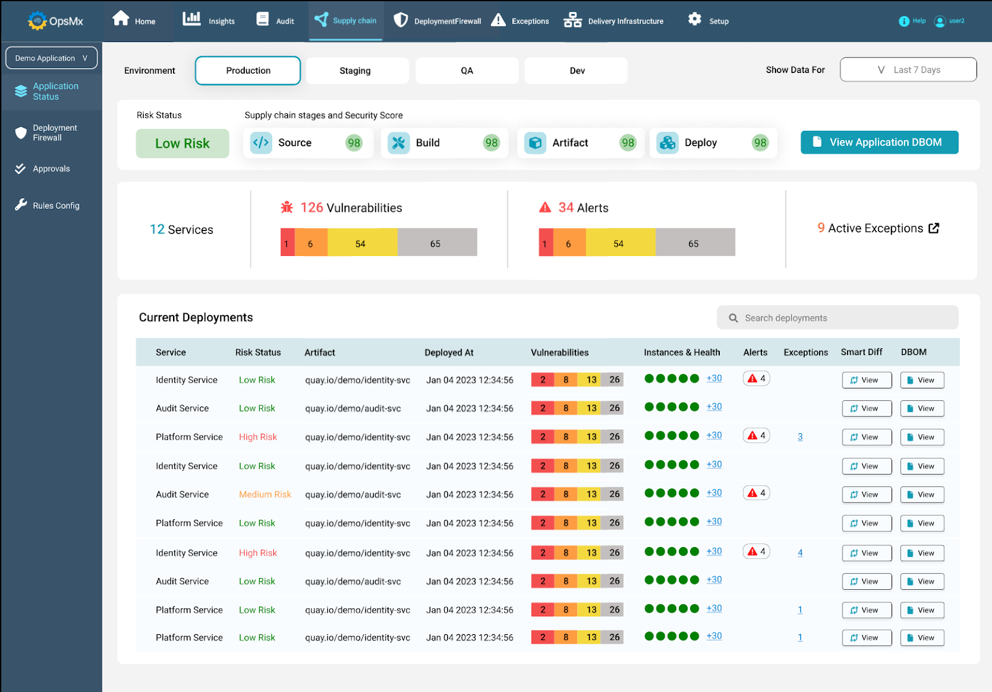
The effectiveness of AppSec Posture depends on performing regular vulnerability scans on your applications. The reports from these scans will determine vulnerabilities or configurational issues of your software application.
The configuration of ASPM tools or the scanning tools is more critical than the use of these tools. A lot of these scanning tools come with built-in security checks and you can verify if the checks conforming to best practices are met during the build. If the enterprise requires custom extensions to the Sonarqube then you can verify if these checks passed.
Centralized or Decentralized Management of Security Policies
There are two scenarios depending upon the complexity and scale of operations within an enterprise.
One scenario is that the tools are generally configured by the central teams, they are used by devops teams in their delivery pipelines.
The other scenario is that different application teams are responsible for their own workflows and SLAs and for that they may use the tools of their choice or convenience.
In both the scenarios the comprehensiveness of the vulnerability and subsequent analysis depends on the checks that may also include the parameters/ options passed to the tools during the delivery process, besides the preconfigured checks.
These parameters/ options will require additional integrations in your delivery process to fetch the data.
Once you have the data, policies are customizable to verify the required parameters based on the environment or type of application.
Prioritization of Vulnerabilities and Exception Management
Some vulnerabilities will affect application users while others will not have an impact. Not all vulnerabilities are equal and hence you need to prioritize them.
Focus on fixing the ones that have the biggest impact on the business.
And, consider extensions in your ASPM tool for exception management of vulnerabilities as most of the tools do not have an inbuilt mechanism for exception management or related workflow to approve an exception.
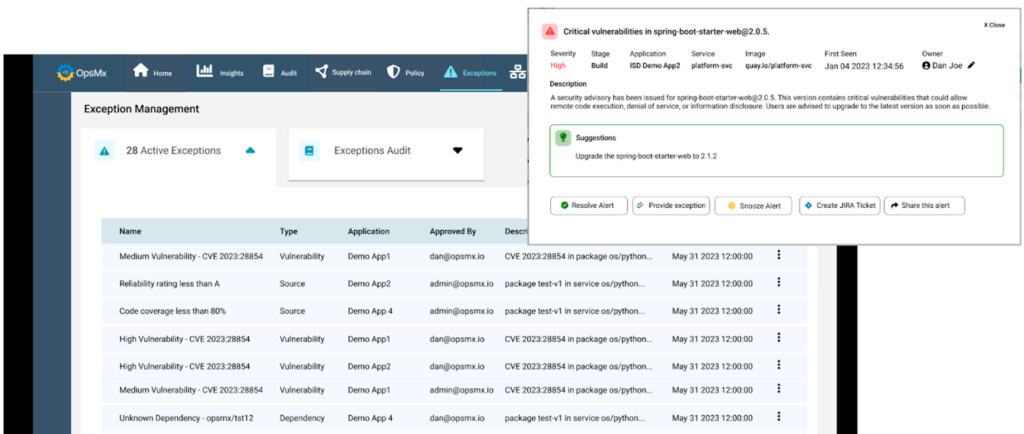
Automated Remediation
Some ASPM tools offer inbuilt vulnerability remediation capabilities. You may use them to fix certain types of vulnerabilities and misconfiguration issues.
Vulnerability Tracing in Production and Incident Response
Prepare for the worst – Incidents can’t be avoided!
As soon as a new vulnerability is discovered, you should have a mechanism to identify and trace that vulnerability running in production for faster remediation and reduced MTTR.
Continuously monitor applications for new vulnerabilities and changes in their security posture. ASPM tools help automate this process.
However, you need to have a robust database providing information about vulnerabilities associated with your SBOM. The extension to your existing ASPM can help achieve this.
Advance Strategies to Apply Rolling Updates To Remove Vulnerabilities in Production
While ASPM will help you in resolving a security vulnerability, you still need to apply a fix to the production environment.
Mostly, enterprises depend on a patch mechanism to address known vulnerabilities promptly.
However, ideally, this mechanism should be automated and follow advanced deployment strategies like Blue-green, canary, or rolling updates. This helps you to validate fixes using automated verification or policy checks during deployments. These strategies should be supported as a part of your existing Continuous Delivery (CD) software. Alternatively, you can obtain extensions on your existing CD to support these strategies without the need of writing any code on top of your existing CDI/CD tool.
Compliance and Reporting
Compliance standards and Regulatory requirements vary from region, industry and business practice. Enterprises may have a set of standards as well as customer requirements for compliance.
At a basic level ASPM tools help ensure your application meets those compliance requirements and provide necessary reports to the auditors.
However, it’s not that simple. Often enterprises have to fetch data from logs and at times may struggle to obtain proof points of compliances that auditors require. This is a painful and time consuming process.
Specific extensions to the existing ASPM tools help generate reports along with the proof points along with the report. The compliance requires three key elements – a set of compliance rules (ideally out of the box), data (source or truth or the proof points, and an enforcement layer (to orchestrate rules within a stage and have an automated decision / approval to ensure compliance).
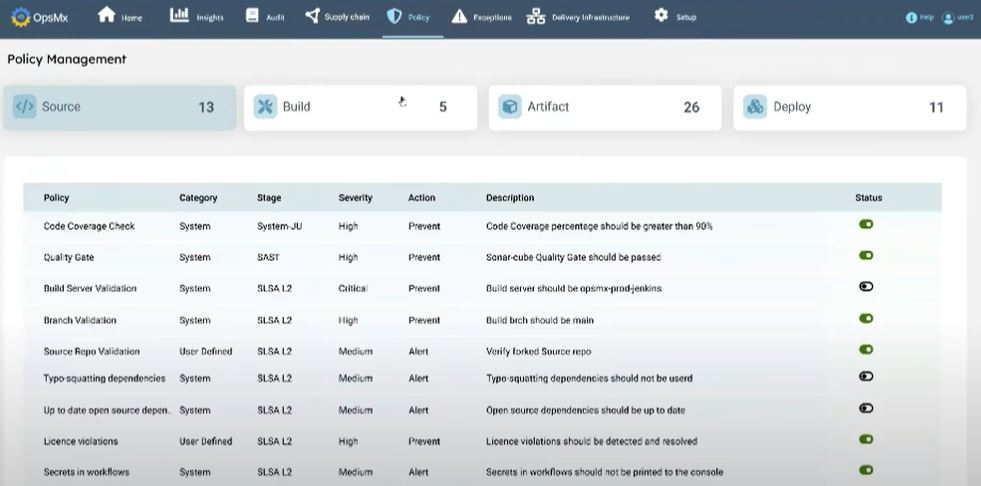
In doing so you need to figure out whether the tool offers these rules out of the box besides the capability to define a custom rule with the help of a rule gene. You may want to refer to this blog on SDLC Compliance Management using policy enforcement on CI/CD pipelines.
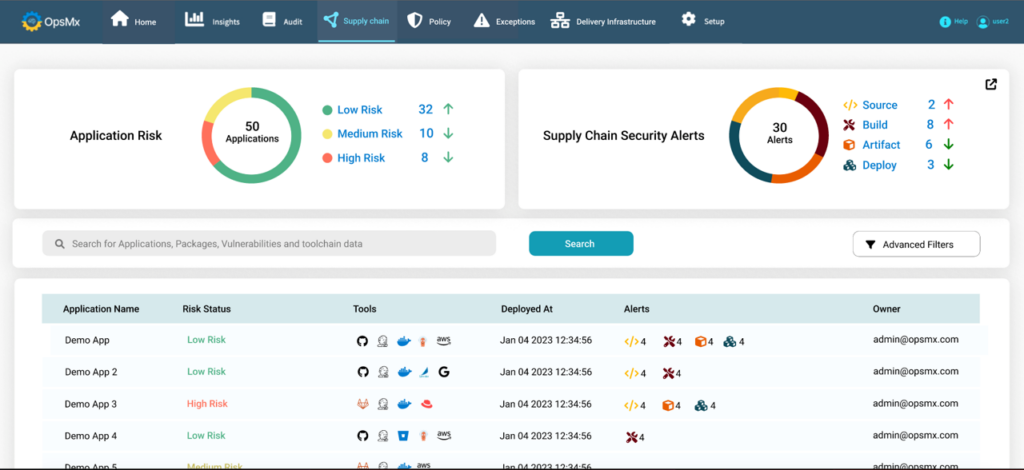
DevSecOps Control Plane
While ASPM tools provide insights into the security posture of your application, it’s extremely important to get insights into the overall organization’s application security risk.
An executive dashboard with a 360 degree view of security posture for all applications as well as drill down capabilities is a must.
A DevSecOps control plane sits as a layer on top of your existing tools to help you extract, represent data, analyze information and provide actionable intelligence that you can leverage to automate vulnerability remediation.
Continuous Improvement
This is not a specific step but a logical practice. As application security is evolving, you should continuously evaluate the effectiveness of your ASPM program and improvize as it evolves.
You may be wondering about certain elements of this blog written using italics. I’ve done this purposefully to get you attention to certain must-have capabilities to offer completeness and robustness to your ASPM program. While these capabilities aren’t available in all ASPM tools out of the box, these can be obtained from OpsMx Deploy Shield. The Deploy Shield enables secure software delivery and enforces compliance to your overall SDLC process. It ensures that you deliver better software faster with all the desired security and compliance controls in place.

0 Comments